Difference between revisions of "Draft: PEC-Hybrid/Current/Admin/About"
| Line 147: | Line 147: | ||
|freetext=A transaction object is needed for Genesys components to authenticate with Genesys Cloud. | |freetext=A transaction object is needed for Genesys components to authenticate with Genesys Cloud. | ||
<ol> | <ol> | ||
| − | <li>Create a transaction object (and alias) of type '''list''' named '''hybrid_integration''' in the ''' | + | <li>Create a transaction object (and alias) of type '''list''' named '''hybrid_integration''' in the '''Transaction''' folder of the '''Environment''' tenant. |
<ul> | <ul> | ||
| − | |||
<li>Tenant characteristics: | <li>Tenant characteristics: | ||
<ul> | <ul> | ||
| − | <li>'''Single tenant deployment''': If your PureEngage deployment is ''not'' multi-tenant, the transaction object should be | + | <li>'''Single tenant deployment''': If your PureEngage deployment is ''not'' multi-tenant, the transaction object should be in the '''Transaction''' folder in the '''Environment''' or '''Resources''' structure.</li> |
| − | <li>'''Multi-tenant deployment''': If your PureEngage deployment is multi-tenant, there must be a separate transaction object under ''each'' of the tenant structures. The transaction objects represent the connectivity to the different PureCloud Orgs representing these different tenants. You ''cannot'' place a transaction object in the Environment structure and share it across tenants because you need a separate PureCloud Org for each tenant.</li> | + | <li>'''Multi-tenant deployment''': If your PureEngage deployment is multi-tenant, there must be a separate transaction object under ''each'' of the tenant structures. The transaction objects represent the connectivity to the different PureCloud Orgs representing these different tenants. You ''cannot'' place a transaction object in the Environment structure and share it across tenants because you need a separate PureCloud Org for each tenant. |
| + | {{NoteFormat|If you are running Workspace Desktop Edition 8.5.133.02, you must ensure that the agents of a Tenant do ''not'' have READ access on the 'hybrid_integration' Transaction objects of the ''other'' tenants.|3}} | ||
| + | </li> | ||
</ul> | </ul> | ||
</li> | </li> | ||
| Line 162: | Line 163: | ||
<li>'''organization_sname''': The PureCloud organization short name for this tenant.</li> | <li>'''organization_sname''': The PureCloud organization short name for this tenant.</li> | ||
<li>'''organization_id''': The PureCloud organization id for this tenant.</li> | <li>'''organization_id''': The PureCloud organization id for this tenant.</li> | ||
| − | <li>'''default_agent_role_name''': The default PureCloud agent role name for an AI agent. This will always be '''employee''' | + | <li>'''default_agent_role_name''': The default PureCloud agent role name for an AI agent. This will always be '''employee'''. </li> |
<li>'''default_admin_role_name''': The default PureCloud admin role name. This is '''admin'''.</li> | <li>'''default_admin_role_name''': The default PureCloud admin role name. This is '''admin'''.</li> | ||
| − | <li>'''base_auth_url''': The base auth URL that can be used for any PureCloud service; for example: '''base_auth_url''' should be <nowiki>https://[region_host]/oauth/token</nowiki>. <nowiki>[region_host]</nowiki> is the authentication-based FQDN for the region; the regions are listed on [https://developer.mypurecloud.com/api/rest/ this page].</li> | + | <li>'''base_auth_url''': The base auth URL that can be used for any PureCloud service; for example: '''base_auth_url''' should be <nowiki>https://[region_host]/oauth/token</nowiki> (for example: <nowiki>"https://login.mypurecloud.com/oauth/token"</nowiki>). <nowiki>[region_host]</nowiki> is the authentication-based FQDN for the region; the regions are listed on [https://developer.mypurecloud.com/api/rest/ this page].</li> |
<li>'''base_service_url''': The base URL that can be used for any PureCloud service; for example: '''base_service_url''' should be <nowiki>https://[region_host]/api/</nowiki>. <nowiki>[region_host]</nowiki> should be the API-based FQDN for the region; the regions are listed on [https://developer.mypurecloud.com/api/rest/ this page]. The rest of the URL is PureCloud service and version specific; for example: '''...v2/conversations'''. The '''base_service_url''' and the service specific portion is combined in your component code.</li> | <li>'''base_service_url''': The base URL that can be used for any PureCloud service; for example: '''base_service_url''' should be <nowiki>https://[region_host]/api/</nowiki>. <nowiki>[region_host]</nowiki> should be the API-based FQDN for the region; the regions are listed on [https://developer.mypurecloud.com/api/rest/ this page]. The rest of the URL is PureCloud service and version specific; for example: '''...v2/conversations'''. The '''base_service_url''' and the service specific portion is combined in your component code.</li> | ||
</ul> | </ul> | ||
| Line 171: | Line 172: | ||
<ul> | <ul> | ||
<li>'''issuer''': The SAML IDP URI that you created in the PureCloud Provisioning steps above (for example: <nowiki>https://www.genesys.com/pureengage</nowiki>).</li> | <li>'''issuer''': The SAML IDP URI that you created in the PureCloud Provisioning steps above (for example: <nowiki>https://www.genesys.com/pureengage</nowiki>).</li> | ||
| − | <li>'''certificate''': The public key of the SAML related certificate (a base64 saml.pem PEM encoded key).</li> | + | <li>'''certificate''': The public key of the SAML related certificate (a base64 saml.pem PEM encoded key; for example: saml.pem.b64 created in step xx).</li> |
| − | <li>'''pkey''': The encrypted SAML related certificate private key (a saml.pkcs8 private key encrypted in aes256 with a password (see password option below) and encoded in base64). You must encrypt the private key with a password that you create before you store the key in Config Server.</li> | + | <li>'''pkey''': The encrypted SAML related certificate private key (a saml.pkcs8 private key encrypted in aes256 with a password (see password option below) and encoded in base64; for example: key.pem.enc.b64 created in step xx). You must encrypt the private key with a password that you create before you store the key in Config Server.</li> |
| − | <li>'''password''': The password to decrypt the private key | + | <li>'''password''': The password to decrypt the private key that you specified in step xx.</li> |
<li>'''expire_time''': The expiration time (in hours) for the access token. The default is 24 hours. This might be overridden on the server side.</li> | <li>'''expire_time''': The expiration time (in hours) for the access token. The default is 24 hours. This might be overridden on the server side.</li> | ||
</ul> | </ul> | ||
| − | + | For each PureEngage service that uses a PureCloud common service (specified at step#1) you must create a dedicated section in the Transaction object: | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
<ul> | <ul> | ||
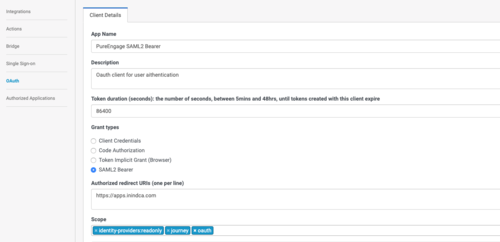
| − | <li>Create the following Object options in the '''saml_auth''' section for the OAuth client for SAML Authentication from the client (such as Workspace Desktop Edition): | + | <li>Create the following Object options in the '''saml_auth''' section for the OAuth client for SAML Authentication from the client (such as Workspace Desktop Edition) that you created in step 1a of type SAML2 Bearer: |
<ul> | <ul> | ||
| − | <li>'''client_id'''</li> | + | <li>'''client_id''': The SAML2 Bearer client ID created in step 1a</li> |
| − | <li>'''password'''</li> | + | <li>'''password''': The SAML2 Bearer client secret created in step 1a</li> |
</ul> | </ul> | ||
</li> | </li> | ||
| − | <li>For | + | <li>For the Agent Pacing Service, create the following Object options in the '''ewt''' section for the pacing engine to connect to PureCloud: |
<ul> | <ul> | ||
| − | <li>'''client_id'''</li> | + | <li>'''client_id''': The Client Credential Grant Client ID that you created in step 1b.</li> |
| − | <li>'''password'''</li> | + | <li>'''password''': The Client Credential Grant Client secret that you created in step 1b.</li> |
</ul> | </ul> | ||
</li> | </li> | ||
Revision as of 16:47, June 4, 2019
{{Article |Standalone=Yes |DisplayName=Provisioning PureEngage Hybrid Integrations |Platform=PureEngage |TocName=Provisioning |ComingSoon=No |Context=This article describes the essential provisioning steps to enable a hybrid integration between PureEngage On-Prem deployments and Genesys PureCloud services. |Section=
Contents
Supported Services
About Provisioning
{{Section
|sectionHeading=PureCloud Provisioning Steps |Type=Unstructured |freetext=Perform the following steps using the PureCloud Admin UI or the PureCloud API.
- To allow for better control and monitoring of the components using PureCloud Services, for each PureEngage Service that uses a common service you must create an OAuth client to allow for better control and monitoring of the components using the PureCloud Services and for different rate limiting per client. This does not mean that if you have n number of components on premises that are associated with one another, they cannot share a given client id.
Genesys recommends that you consult architecture before performing this step.
- Create a SAML2 Bearer OAuth Client for the client, such as PureEngage Workspace Desktop Edition, that needs to send a SAMLResponse to exchange for a PureCloud Access Token:
- As necessary, for each on-premises service, like the "Agent Pacing Service" (ewt), create OAuth Client Credentials grants:
- Using the UI, follow these steps,
- Or using the API, reference these endpoints.
For more information about Permissions for Altocloud, see the Altocloud permissions overview.
- Create your SAML Cert and key. Certificate is base64 string created from PEM file by using this command:
openssl req -new -x509 -days 3652 -nodes -out saml.crt -keyout saml.pem
Pkey is also based64 string but requires additional command to create encrypted private key:
openssl pkcs8 -topk8 -inform PEM -outform PEM -in saml.pem -out key.pem -nocrypt
Once you have created the two PEM files perform the following steps:
- Encode saml.pem into a base64 string (=>’saml.pem.b64’) using this command:
openssl base64 -in saml.pem -out saml.pem.b64
- Encrypt the key.pem using a password that you specify
openssl rsa -in key.pem -out key.pem.enc -aes256
- Encode the resulting content into a base64 string (=>’key.pem.enc.b64’) using this command:
openssl base64 -in key.pem.enc -out key.pem.enc.b64
- Encode saml.pem into a base64 string (=>’saml.pem.b64’) using this command:
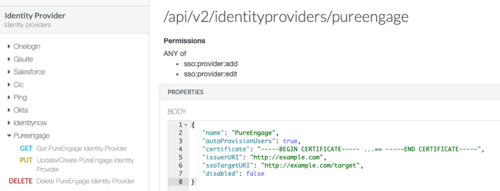
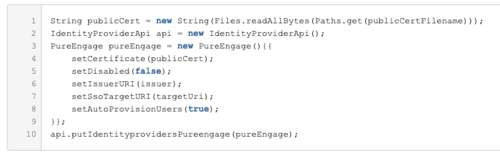
- Create a PureEngage Identity Provider (IDP). You can use the Identity Provider API via the PureCloud Developer Tools, SDKs, or Platform API.
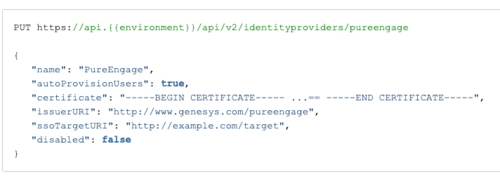
Sample Request:
PUT https://api.{{environment}}/api/v2/identityproviders/pureengage { "name": "PureEngage", "autoProvisionUsers": true, "certificate": "Content of the saml.pem file", "issuerURI": "http://www.genesys.com/pureengage", "ssoTargetURI": "http://example.com/target", "disabled": false }Troubleshooting:
- Ensure that the IDP is set with "autoProvisionUsers" = "true"
- Ensure that the issuer URI in your SAML assertion is the same as the issuer URI for the IDP.
- Ensure that you don't have multiple issuers with the same URI.
- By default, Altocloud permissions are included in the Admin and AI Agent roles. As auto-provisioned users are created with the employee role, which does not include Altocloud permissions. You must grant the [Altocloud permissions to the employee role. You may grant Altocloud permissions to additional roles as needed.
- (Optional as needed) Create additional Admin accounts by adding people to your organization and assigning them to the Admin role.
|Status=No }}
PureEngage On Premises: Transaction object for hybrid integrations
Opening Your Network
}}